2023 Cybersecurity Report
Technology permeates every facet of our lives, including our work lives. Because of this, cybersecurity has become essential. As our reliance on interconnected systems and data-driven processes increases, so do the threats lurking in the shadows. In fact, global cyberattacks increased 38% in 2022. To navigate this ever-evolving landscape, it is crucial to stay informed about the latest cybersecurity news and statistics. By shedding light on emerging trends and highlighting noteworthy incidents, we aim to equip you with valuable insights into the world of cybersecurity.
Let’s start with some of the latest statistics:
- According to CrowdStrike, “After some of the biggest and most notorious ransomware enterprise shutdowns, ransomware affiliates moved to new ransomware-as-a-service (RaaS) operations.” What is RaaS? It’s a business model between ransomware operators and affiliates where the affiliate, who has less skill or time, pays to launch a ransomware attack developed by the operators.
- In 2023, CrowdStrike Intelligence, a company focused on securing endpoints, cloud workloads, identity, and data, began tracking 33 new adversaries, malicious actors or groups that attempt to gain unauthorized access to systems or networks, bringing the total number to over 200 who are currently being tracked.
- Most tracked adversaries come from Eastern Europe and Russia; however, others are being tracked in different regions including Asia.

- In 2022 access brokers, those who get access to an organization and then provide or sell this access to others, targeted the following verticals, in order of frequency: academic, technology, industrial, manufacturing, professional services, finance, government, healthcare, and retail.
- Malware-free activities accounted for 71% of all detections in 2022, up 9% from 2021. This simply means that the attackers have not installed anything into the system and are running in memory – making them harder to detect. Because malware has become easier to detect with anti-virus software, cybercriminals are now going malware-free to stay undetected for longer.
- Two newly named adversaries – Slippy Spider and Scattered Spidar – pushed limits by targeting high-profile victims which affected their employees, customers, and partners.
- 43% of cyber attacks are aimed at small businesses with only 14% of this sector prepared to defend against one.
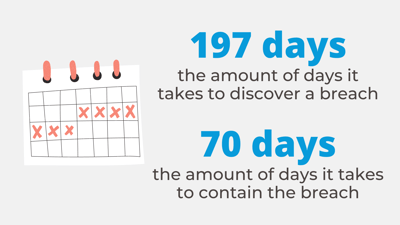
- It takes roughly 197 days to discover a network breach and almost 70 days to contain it.
- 74% of data breachers involved a human element – social engineering attacks, errors, or misuse.
Cyberattacks of 2023
- T-Mobile was once again the target of an attack that saw customer data accessed through a vulnerable application programing interface (API) in January. Data included payment card information and social security numbers.
- Also in January, the Tucson Unified School District in Southern Arizona, the largest school districts in the state, was the victim of a ransomware attack that encrypted their data and threatened to publish stolen data if they were not paid. This impacted 42,000 students and 7,000 staff members.
- In February, an unconfirmed ransomware attack shut down IT systems at Tallahassee Memorial Hospital for weeks. Surgeries were rescheduled and patients were re-directed to other facilities.
- Additionally, Cloudflare thwarted off the largest known distributed denial-of-service (DDoS) attack. The goal of the attack was to access gaming platforms, cryptocurrency companies, and hosting providers that use Cloudflare and disrupt normal traffic to the server.
- Between February and March of 2022, Slippy Spider targeted Microsoft, Nvidia, Okta, and Samsung. They leaked data including source code, employee credentials and more. Though a ransom was demanded, there is no evidence it was met.
- U.S. Federal Government Agencies, including the U.S. energy department, were the victim of a global cyber attack by Russian cybercriminals in June. They exploited a vulnerability in MOVEit, a managed file transfer software that encrypts data in rest and in motion.
It is clear that cybercriminals are moving quickly to take advantage of vulnerabilities and new techniques to stay undetected. The statistics underscore the gravity of the situation we, as businesses and organizations, are in. Organizations of all sizes need to not only have cybersecurity technology in place but also focus on training their employees to be cyber-aware. Taking the proper precautions now can greatly reduce your risk of becoming a cyber statistic.
Be proactive in your approach to cybersecurity.
You may also be interested in the following articles:
5 Ways to Secure Your Printer
Two-Factor Authentication: What is it and Why Do You Need It?
A New Year’s Audit – Get a Risk Assessment of Your IT Systems
Protecting Your Data in the New Year
Training your employees to be “cyber aware”
Common Password Mistakes that Put You At Risk
Best Practices for Identifying Phishing



